Organizations for B2B Single Sign-On OIDC & SAML
- New to Ory? Talk to the team about features and plans.
- Already a customer? Open a support ticket.
Organizations are a way to group users within one project. An organization always belongs to one Ory project. Within a project, an identity can belong to an organization or remain without an organization. Organizations contain multiple OIDC or SAML SSO connections. All members of an organization must use one of the organization's OIDC or SAML SSO connections to log in.
An organization can have multiple domains. Registrations for email addresses with a domain that belongs to an organization must go through one of the organization's OIDC or SAML SSO connections.
Some identity providers do not validate email domain ownership. This can lead to situations where Organization login is configured
for a specified domain such as @example.com, but due to this lack of this email domain ownership validation by the identity
provider, a users with other email domains such as @gmail.com can still authenticate successfully via the identity provider.
This will end up with the user being part of the configured organization in your Ory project, even if the domain does not match any of the configured domains.
Organizations require identifier-first authentication and two-step registration when using Account Experience 2.x or Ory Elements 1.x.
Manage organizations
- Ory Console
- API
To create, update, or delete organizations via the Ory Console, go to
Authentication → Organizations in the Ory Console.
Organizations can also be managed using the Ory API. To authenticate your requests, create a workspace API key.
All examples below use curl to make HTTP requests. You can use any HTTP client to make these requests.
Before copy & pasting the following examples, export your PROJECT_ID and WORKSPACE_API_KEY:
export PROJECT_ID="..."
export WORKSPACE_API_KEY="ory_wak_..."
List organizations
curl -X GET --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations" \
-H "Authorization: Bearer $WORKSPACE_API_KEY"
Create an organization
curl -X POST --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '{
"label": "Hello demo",
"domains": ["test.example.com"]
}'
Get an organization
curl -X GET --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations/$ORGANIZATION_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY"
Delete an organization
curl -X DELETE --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations/$ORGANIZATION_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY"
Create SSO connections for an organization
After creating an organization, continue by adding one or more SSO OIDC connections.
- Ory Console
- API
Go to Authentication → Organizations in the Ory Console and continue by configuring the selected organization.
The SSO connections are part of the project configuration. To authenticate, use the same workspace API key as for managing organizations. The examples use curl to make HTTP requests and jq to parse JSON response.
Create an SSO connection
curl -X PATCH --location "https://api.console.ory.sh/projects/$PROJECT_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '[
{
"op": "add",
"path": "/services/identity/config/selfservice/methods/oidc/config/providers/-",
"value": {
"client_id": "...",
"client_secret": "...",
"id": "ory-GPx1yPH4",
"issuer_url": "https://example.org",
"label": "My OIDC provider",
"mapper_url": "base64://ZnVuY3Rpb24oY3R4KSBjdHg=",
"organization_id": "6bb1c7d1-3b3e-4995-9e09-35649dc45a2b",
"provider": "generic",
"pkce": "auto", # or "force", "never", see note on redirect URL below
"scope": ["openid", "offline_access", "email"]
}
}
]' \
| jq ".project.services.identity.config.selfservice.methods.oidc.config.providers"
Some notes on the fields of the JSON payload:
client_idandclient_secretare the credentials of the OIDC provider.idis a unique identifier for the connection, and part of the redirect URL, and can be a random string. This is$PROJECT_IDbelow.organization_idis the ID of the organization to which the connection belongs, and part of the redirect URL. This is$ORGANIZATION_IDbelow.mapper_urlis the URL to a JSONnet file that maps the OIDC provider's claims to Ory's identity schema. You can use thebase64scheme to embed the JSONnet file directly in the JSON payload.pkcedetermines whether Ory Identities will use PKCE during the OIDC flow. See the note below and the PKCE documentation for details.
The redirect URL to be set in the external OIDC provider's configuration is
https://$PROJECT_SLUG.projects.oryapis.com/self-service/methods/oidc/organization/$ORGANIZATION_ID/callback/$PROVIDER_ID.
If you set pkce: force, you must whitelist a different redirect URL with the OIDC provider:
https://$PROJECT_SLUG.projects.oryapis.com/self-service/methods/oidc/callback.
See the PKCE documentation for details.
List SSO connections
curl -X GET --location "https://api.console.ory.sh/projects/$PROJECT_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
| jq ".services.identity.config.selfservice.methods.oidc.config.providers"
Result:
[
{
"client_id": "...",
"client_secret": "...",
"id": "ory-GPx1yPH4",
"issuer_url": "https://example.org",
"label": "My OIDC provider",
"mapper_url": "https://storage.googleapis.com/bac-gcs-production/94292215dbabe405bebff988b5356663fcf5cba35b10fc6ca2cfea7bc7049e906e01d271a3daeb844203efdfbf2cff356274daa63d5afc2a379bbe93b8b40e63.jsonnet",
"organization_id": "6bb1c7d1-3b3e-4995-9e09-35649dc45a2b",
"provider": "generic",
"scope": ["openid", "offline_access", "email"]
}
]
Delete an SSO connection
To delete an organization, you need to specify the index of the connection in the path field. The index is the position of the
SSO connection in the list of connections.
curl -X PATCH --location "https://api.console.ory.sh/projects/$PROJECT_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '[
{
"op": "remove",
"path": "/services/identity/config/selfservice/methods/oidc/config/providers/0"
}
]' \
| jq ".project.services.identity.config.selfservice.methods.oidc.config.providers"
Note that the organization_id field contains the organization ID to which the connection belongs.
See it live
After having set up everything, go to your registration page. Entering an email that ends with the organization's domain, such as
@my.example.com from the example above, shows a Sign in with SSO button instead of the password field. Clicking it will take
you to sign in with the SSO connection. The SSO connection is not visible for email addresses that are not managed by the
organization.
Pre-provisioning identities in an organization
After creating an organization, you can pre-provision identities in it. This is useful when you need to create related data in your system but need the identity to be created in Ory Network first, before the user logs in for the first time.
To achieve this, set the organization_id property to the ID of the created organization in the identity, either when creating
the identity, or by updating the identity's data using the Ory APIs.
SAML
SAML (Security Assertion Markup Language) is an XML-based open standard used for exchanging authentication and authorization data between parties. The SAML integration in Ory Network uses the B2B Organization feature.
SAML via Ory Network
This guide will walk you through the steps required to set up SAML Single Sign-On (SSO) with Ory Network.
Prerequisites
Before proceeding, ensure you are on a plan that supports SAML SSO. SAML is available exclusively on select Enterprise plans. Contact us if you need SAML support.
- Ory Console
- API
- Go to Authentication → Organizations in the Ory Console to create an organization.
- Select "Add a new Enterprise SAML SSO connection" and follow the instructions to configure the SAML connection. Fill out the following form fields:
- Label: A descriptive name for the SAML connection. This will be displayed to users.
- Data mapping: A mapping from the SAML attributes to Ory's identity schema.
- Raw IDP metadata XML: The XML metadata file from your SAML Identity Provider (IdP).
- Navigate to your login screen to test the SAML connection.
Create an organization
curl -X POST --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '{
"label": "SAML organzation",
"domains": ["example.com"]
}'
Enable SAML authentication
curl -X PATCH --location "https://api.console.ory.sh/projects/$PROJECT_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '[
{
"op": "replace",
"path": "/services/identity/config/selfservice/methods/saml/enabled",
"value": true
}
]' \
| jq ".project.services.identity.config.selfservice.methods.saml"
Create a SAML connection
curl -X PATCH --location "https://api.console.ory.sh/projects/$PROJECT_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '[
{
"op": "add",
"path": "/services/identity/config/selfservice/methods/saml/config/providers/-",
"value": {
"id": "some-provider-id",
"label": "My SAML provider",
"mapper_url": "base64://...",
"raw_idp_metadata_xml": "base64://...",
"organization_id": "$ORGANIZATION_ID"
}
}
]' \
| jq ".project.services.identity.config.selfservice.methods.saml"
- label: A descriptive name for the SAML connection. This will be displayed to users.
- mapper_url: A mapping from the SAML attributes to Ory's identity schema.
- raw_idp_metadata_xml: The XML metadata file from your SAML Identity Provider (IdP).
The SAML application callback URL to set at our SAML Identity Provider is: https://api.console.ory.sh/saml/api/oauth/saml
Data mapping
You can configure the mapping of SAML attributes to Ory's identity schema using Jsonnet. All custom SAML attributes defined at the
Identity Provider (IdP) will be available in the raw_claims object within claims. These attributes can then be mapped to the
Ory identity schema.
Ensure that the appropriate identity schema is created before mapping attributes. The email attribute is natively available in
claims.email, everything else is nested under claims.raw_claims.
Example SAML data mapping
Mapping firstName and lastName from the SAML Identity Provider to the Ory identity schema (traits).
local claims = std.extVar('claims');
{
identity: {
traits: {
email: claims.email,
[if std.objectHas(claims, "raw_claims") && std.objectHas(claims.raw_claims, "firstName") then "firstName" else null]: claims.raw_claims.firstName,
[if std.objectHas(claims, "raw_claims") && std.objectHas(claims.raw_claims, "lastName") then "lastName" else null]: claims.raw_claims.lastName,
},
},
}
Self-service organization onboarding
- New to Ory? Talk to the team about features and plans.
- Already a customer? Open a support ticket.
The onboarding portal is a powerful tool designed to simplify complex identity and access management tasks for businesses and their partners.
Streamline organization onboarding
The onboarding portal simplifies setting up and managing identity connections with external organizations.
The onboarding portal aims to:
- Simplify complex integrations: A self-service or guided experience removes the need for client IT administrators to be SAML/SCIM experts.
- Reduce onboarding time: External administrators configure connections directly through a user-friendly interface instead of lengthy manual setup and back-and-forth communication.
- Enhance security and control: Shareable links don't expose sensitive information. Administrators configure their side securely while maintaining control over their IdP settings.
- Enable self-service: SaaS providers can let customers manage their own SSO/SCIM connections, freeing up engineering and support teams.
- Scale B2B integrations: Manual management becomes unsustainable as enterprise clients grow. The portal provides a scalable solution.
- Validate instantly: Test SSO connections immediately to verify integration before deployment, reducing troubleshooting time.
The onboarding is relevant for SaaS providers serving B2B or B2B2C customers, enterprise IT administrators managing identity providers, and developers building multi-tenant applications.
Provider support:
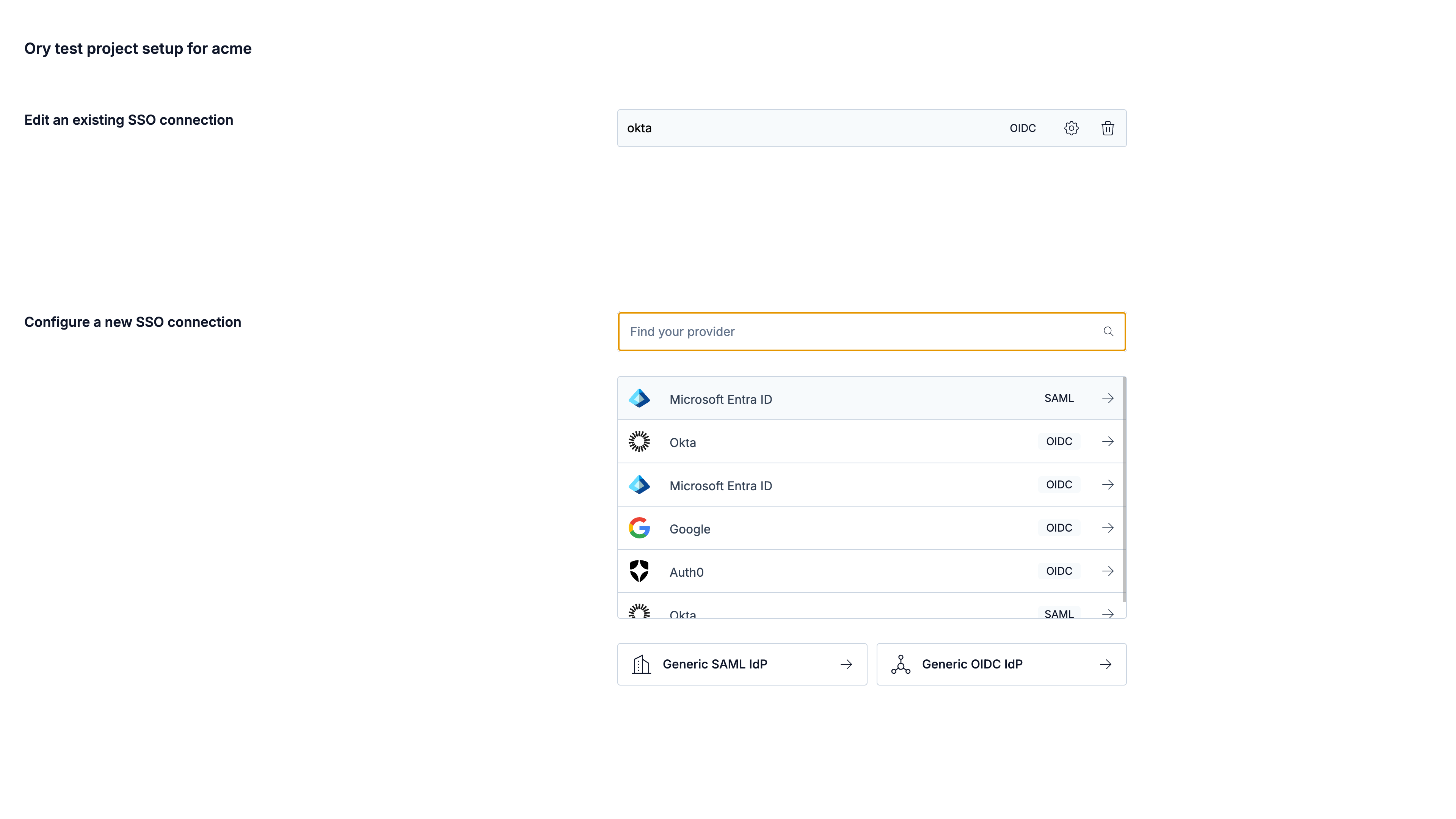
- The onboarding portal supports all well known providers. You can also connect any SAML/OIDC compliant provider using the Generic SAML/OIDC IdP option. If you don't find your provider listed, please contact Ory Support.
SCIM support
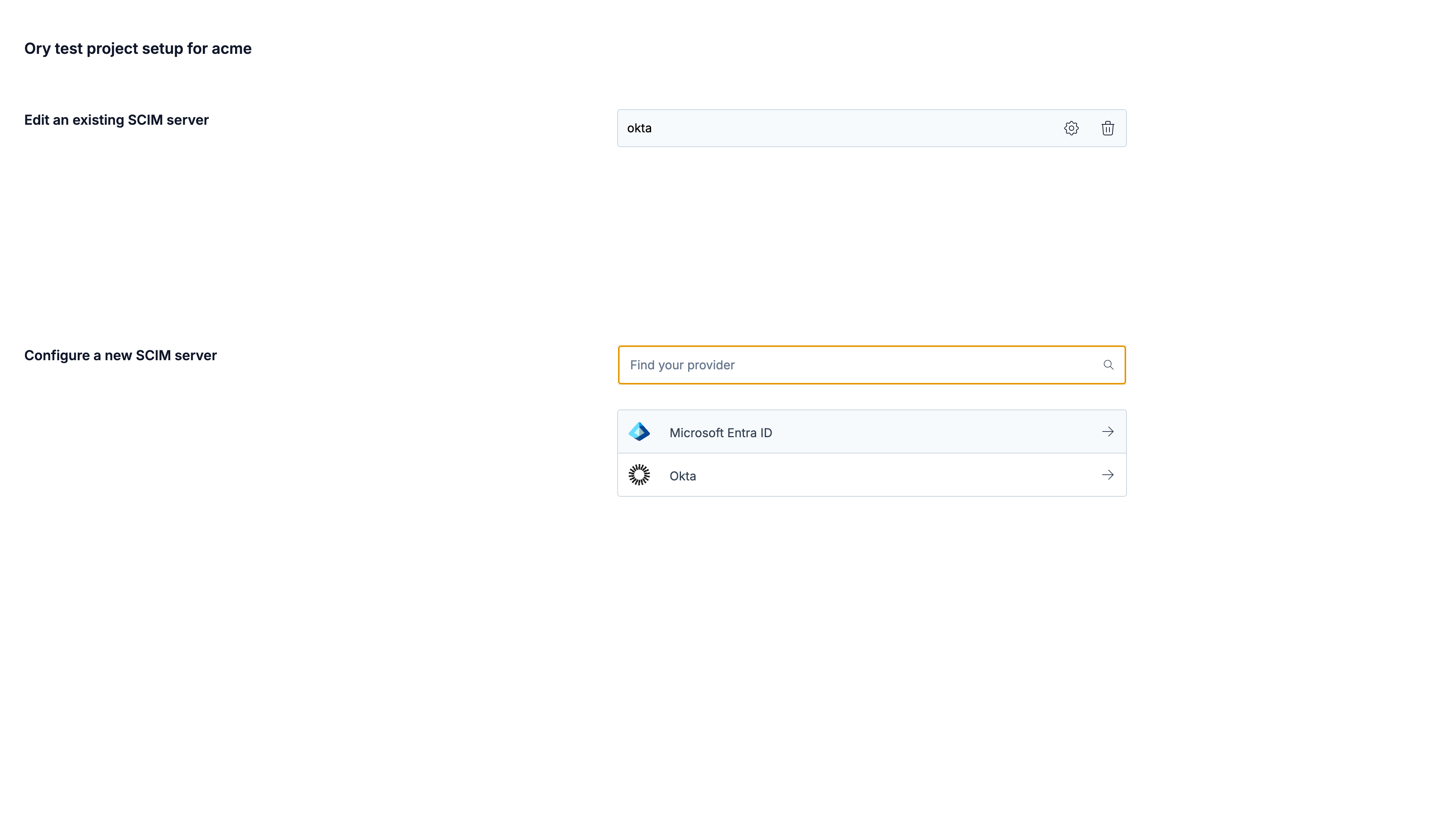
The onboarding portal allows you to set up SCIM provisioning. For an organization, you can create, update, and remove SCIM servers. Guided walkthroughs are available for Microsoft Entra ID, Google Workspace, and Okta.
Manage onboarding portal links
- Ory Console
- API
Create a link
Go to Authentication → Organizations in the Ory Console and continue by configuring the selected organization.
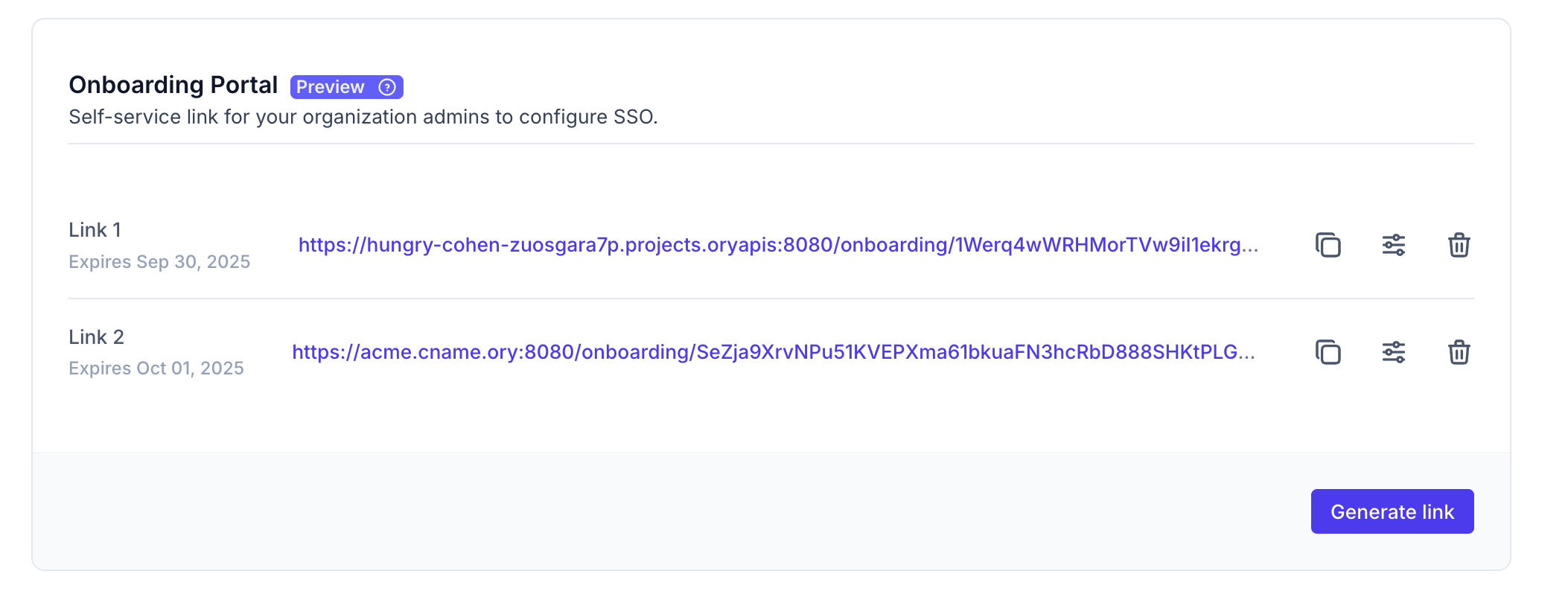
On the Edit Organization page, under the Onboarding Portal section, click Generate link. If your project has a custom domain configured, you must choose between the project slug and the custom domain as the link's base URL. You can then share this link with the organization administrators.
Onboarding portal links can also be managed using the Ory API. To authenticate your requests, create a workspace API key. All examples below use curl to make HTTP requests. You can use any HTTP client to make these requests. Before copy & pasting the following examples, export your PROJECT_ID,ORGANIZATION_ID and WORKSPACE_API_KEY:
Create an onboarding portal link
curl -X POST --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations/$ORGANIZATION_ID/onboarding-portal-links" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '{
"expires_at": "2025-06-01T00:00:00Z",
"enable_sso": true,
"enable_scim": true,
"custom_hostname_id": "use a custom domain id from branding, omit the field otherwise"
}'
Result:
{
"id": "d36ad207-e1a8-4eac-bc1b-c25e223cc15b",
"value": "Fhca7DvuRLjQpDslMpYHMfsqSoy7vbI92PAxNlziZDidGBiW",
"project_id": "836b03f7-fdce-466a-9407-8595a0f615ce",
"organization_id": "517cc5e7-1ab6-4dcf-ba02-00fad003af92",
"enable_sso": true,
"enable_scim": true,
"created_at": "2025-06-02T05:23:45.299988Z",
"expires_at": "2025-06-03T05:23:45Z",
"custom_hostname_id": "aa4c8766-02b8-423a-80d2-47adf8e8c2ca"
}
The response contains a value token that you can use to construct the onboarding portal link as follows:
https://your-slug.projects.oryapis.com/onboarding/<value>
Update an onboarding portal link
curl -X POST --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations/$ORGANIZATION_ID/onboarding-portal-links/$ONBOARDING_PORTAL_LINK_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY" \
-H "Content-Type: application/json" \
-d '{
"expires_at": "2025-06-01T00:00:00Z",
"enable_sso": true,
"enable_scim": true
}'
Result:
{
"id": "655fa1d7-8404-4aa5-a90d-7f0aee060bc6",
"value": "emH8rO0f9S8VtLXLhBdNc9vBPSgsoT3qYHQQd7ROf8HwMmtK",
"project_id": "94d32bfd-08ea-4a11-a026-b9d7ddda0f09",
"organization_id": "9e83d579-ba29-43dd-b245-28c525c82066",
"enable_sso": true,
"enable_scim": true,
"created_at": "2025-08-21T15:48:00.101704Z",
"expires_at": "2027-06-01T00:00:00Z"
}
Delete an onboarding portal link
curl -X DELETE --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations/$ORGANIZATION_ID/onboarding-portal-links/$ONBOARDING_PORTAL_LINK_ID" \
-H "Authorization: Bearer $WORKSPACE_API_KEY"
List onboarding portal links
curl -X GET --location "https://api.console.ory.sh/projects/$PROJECT_ID/organizations/$ORGANIZATION_ID/onboarding-portal-links" \
-H "Authorization: Bearer $WORKSPACE_API_KEY"
Result:
{
"links": [
{
"id": "d6458578-dbeb-45ee-95e7-3b98168ff313",
"value": "eHSoZlTTffFP76ns0DOqBI8CT2daCXqRqO3MSVFi7eEbaRIu",
"project_id": "836b03f7-fdce-466a-9407-8595a0f615ce",
"organization_id": "517cc5e7-1ab6-4dcf-ba02-00fad003af92",
"enable_sso": true,
"enable_scim": true,
"created_at": "2025-06-02T05:44:24.883665Z",
"expires_at": "2025-06-03T05:44:24Z"
}
]
}
Expiry
The link generated from the Ory Network Console expires in 7 days. The API allows you to set an expiration value with a minimum expiry of 1 day. Once the link expires, it no longer works. You can also delete the link and generate a new one.
Handover and using the portal
Once you generate the link, share it with the organization's administrator. They can access this link multiple times until its expiration to manage SSO and SCIM connections.
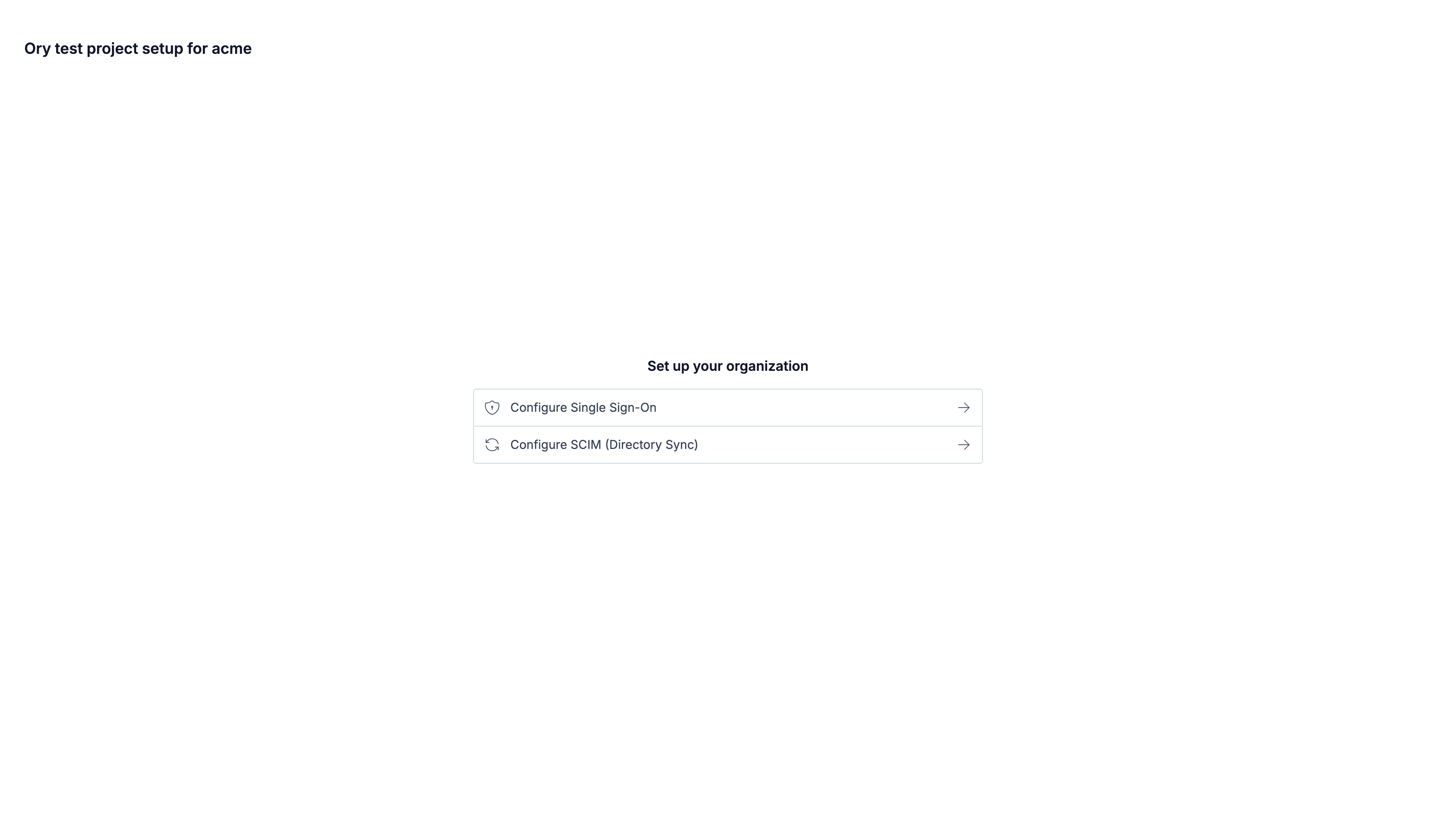
Manage SSO
Manage SCIM